If storing the CSRF token in session is problematic, an alternative defense is a use of a double submit cookie.
what is a double submit cookie
- A double submit cookie is defined as sending a random value in both a cookie and as a request parameter, with the server verifying if the cookie value and request value match.
- When a user authenticates to a site, the site should generate a (cryptographically strong) pseudorandom value and set it as a cookie on the user's machine separate from the session id.
- The site does not have to save this value in any way, thus avoiding the server-side state.
- The site then requires that every transaction request include this random value as a hidden form value (or another request parameter).
- A cross-origin attacker cannot read any data sent from the server or modify cookie values, per the same-origin policy. This means that while an attacker can force a victim to send any value he wants with a malicious CSRF request, the attacker will be unable to modify or read the value stored in the cookie.
- Since the cookie value and the request parameter or form value must be the same, the attacker will be unable to successfully force the submission of a request with the random CSRF value.
[www.owasp.org]
- To understand this tutorial better you may read my Cross-site Request Forgery protection in web applications via Synchronizer Token Patterns post first. [ https://www.blogger.com/blogger.g?blogID=3586283524176614966#editor/target=post;postID=2107125566439437675;onPublishedMenu=template;onClosedMenu=template;postNum=1;src=postname ]
steps to follow
- create a login form.
- create 2 cookies to store the session id and CSRF token.
- create a javascript function to reads the CSRF token cookie value.
- validate values in the form.
First, we need to create 2 cookies
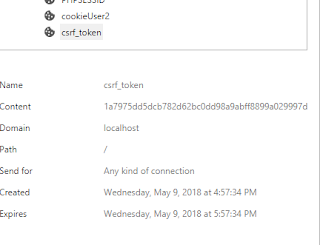
setcookie("csrf_token",$csrf_to,time()+3600,"/","localhost",false,true)
we generate the CSRF token on the client side and store it in a cookie and cookie will set in the browser. The CSRF token value is not stored on the server side.
As you can see CSRF token is now inside a cookie and in the content value of the CSRF token is there.
Then we have to run a javascript to reads the CSRF token cookie value in the browser.
After that, we need to add a new hidden field to the previously created form to get the CSRF token value to that hidden field.
when the form is submitted CSRF cookie will submit and in the hidden field CSRF token value will get submitted.
After submitting the Form if the CSRF token received in the cookie and also in the message body will match we can display a Successful message.








No comments:
Post a Comment