[https://www.owasp.org]
From this tutorial, I'll show you how to secure a Login Form with Synchronizer Token Patterns.
Synchronizer token pattern.
Synchronizer token pattern (STP) is a technique where a token, secret and unique value for each request, is embedded by the web application in all HTML forms and verified on the server side.Steps
- create a login form.
- create a cookie and store the session id
- create CSRF token
- create a javascript function to obtain the CSRF token
- validate values in the form
First, we need to figure out what is the client side and what is the server side.
In client side, we create the login form, javascript, and cookie
in server side, we create CSRF token.
First I created the login form using basic HTML
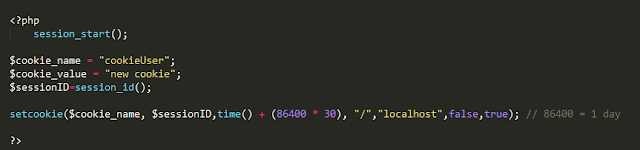
then I created the cookie which users to validate session id with the server side.
What is a Cookie?
Cookies are a mechanism for storing data in the remote browser and thus tracking or identifying return users. You can set cookies using the setcookie() or setrawcookie() function. Cookies are part of the HTTP header, so setcookie() must be called before any output is sent to the browser. Any cookies sent to server from the client will automatically be included in a $_COOKIE
[http://php.net/manual]
In this function, it checks CSRF token and session id is matching with the server and username and the password are correct.
setcookie(name, value, expire, path, domain, secure, httponly);
- Only the name parameter is required. other parameters are optional. but the maximum number of parameters should be 7.
- The secure flag is an option that can be set by the application server when sending a new cookie to the user within an HTTP Response. The purpose of the secure flag is to prevent cookies from being observed by unauthorized parties due to the transmission of the cookie in clear text.
- The browser will not send a cookie with the secure flag set over an unencrypted HTTP request.
- HttpOnly is an additional flag included in a Set-Cookie HTTP response header. Using the HttpOnly flag when generating a cookie helps mitigate the risk of client side script accessing the protected cookie
In this tutorial, I created the cookie using PHP. You can use any language as you prefer.
Note: The
setcookie() function must appear BEFORE the <html> tag.
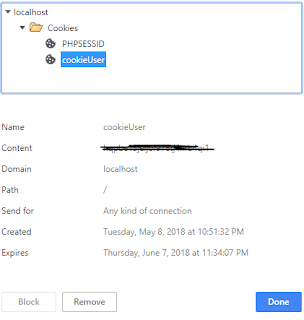
If you created the cookie correctly you can find your cookie in the cookie list after the code executed.
Up to this point, we were on the client side. Now let's create the CSRF token in server side.
- base64_encode(openssl_random_pseudo_bytes(32)) - Generates cryptographically secure pseudo-random bytes
- hash_hmac - Generate a keyed hash value using the HMAC method
After generating the CSRF token we should store the token in the session variable.
$_SESSION['CSRF'] = $csrf_to;
Now let's create a javascript function to obtain the CSRF token via an ajax call. It should create on the client side. From this function, we request the CSRF token from the server side after the client side is loaded.
Ajax can
- Read data from a web server - after the page has loaded
- Update a web page without reloading the page
- Send data to a web server - in the background
- onreadystatechange - Defines a function to be called when the readyState property changes
- readyState - Holds the status of the XMLHttpRequest.
- status - Returns the status-number of a request
[www.w3schools.com]
now we need to call the previously created function in client side
- csrf.php - server-side PHP file
- cst - hidden field name
we need to add a new hidden field to the previously created form that has the value of the received CSRF token.
then you can see there's the CSRF token in the hidden field
when we click on the login button all the information will send to the server side.
Now we should validate the received values of the form by writing a function.
In this function, it checks CSRF token and session id is matching with the server and username and the password are correct.
finally, call the function in server side.
References













No comments:
Post a Comment