Hi, it’s been a while, hope you all doing good. 💓
So today’s article is about a new
ransomware. 😱
Yes. We found a new one. Todarius is its name.
Let’s look into this with more
information.
First of
all what is this TODARIUS?
It’s
a Crypto virus. Crypto viruses are among the most malignant and problematic
forms of malware that can be attacked. Its main objective is to encrypt your
files and that will allow the people behind them to blackmail you for the access
to the encrypted data. If you do not have any important files or a value stored
on your computer, the attack of the Ransom ware crypto virus attack may not be
such a huge issue. But however most of us have at least little amount of
important data in our personal computers. Aren’t we?
How it can
be infects to my computer and what does it do?
Simply it encrypts all of your files. J
It is currently unconfirmed how
exactly this malware get spread. However this ransomware infects through emails
often that carry malicious email attachments or web links. The main idea behind
them is to get users to download and execute files or click on the link. Emails
can make it clear that what a user receives is a legitimate type of message,
and its main purpose is something important. The attachments can be an invoice,
receipt or other important document.
Another form of distribution that can be used by this Ransomware
is probably caused by third party software download sources, fake software
updaters/cracks and Trojans. Freeware download websites, free file hosting
sites, peer-to-peer (P2P) networks, and other unofficial download sources
present malware as legitimate software. These way users get tricked into
downloading and installing malware manually, by themselves

When Ransomware encrypts files, it searches for the most commonly used file types to encode. The encrypted files are usually documents, videos, images, audio and other file formats. Encrypted files contain bytes of your data that are changed to a point that can no longer be opened. The data is encrypted using advanced encryption cipher that generates the decryption key. The files are also appended the .todarius file extension and begin to appear like this:

When Ransomware encrypts files, it searches for the most commonly used file types to encode. The encrypted files are usually documents, videos, images, audio and other file formats. Encrypted files contain bytes of your data that are changed to a point that can no longer be opened. The data is encrypted using advanced encryption cipher that generates the decryption key. The files are also appended the .todarius file extension and begin to appear like this:
When Todarius Ransomware arrives at
your computer, it can recognize by the _readme.txt, which
contains the following text:
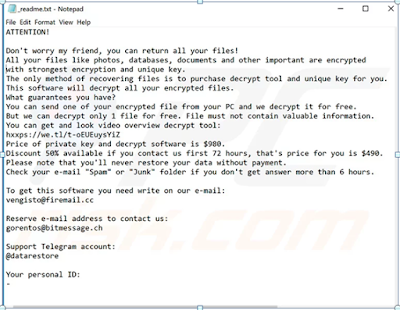 |
| Readme message after the encryption |
Once on your PC, STOP ransomware may drop its payload files
in the following Windows directories:
- ·
%AppData%
- ·
%Local%
- ·
%LocalLow%
- ·
%Roaming%
- ·
%Temp%
Once the files are dropped on the computers of victims, the
ransomware virus could perform the following malicious activities:
- ·
Create mutexes.
- ·
Perform checks if it’s running on a real PC or a
virtual drive.
- ·
Scan for files to encrypt.
- ·
Create registry entries.
- ·
Obtain system information from your computer.
The ransom
payment – is it worth paying for?
In general, the way in which users first learn about the
existence of Ransom ware in their systems and the demand for money issued by
hackers is through an emerging banner that appears on their computer screens.
This logo is created immediately after the end of file encryption, and before
that, you cannot see actual infection symptoms. The message inside the sign
usually indicates that the victim must issue the payment within a specific
period of time, usually two days. There are usually detailed instructions
provided you explain how to pay the money. The usual condition is that the
currency used to make a payment is the Bitcoin currency (or a similar
currency).
If you are currently in this horrible situation and are
wondering if it is really good to pay, know that sending your money will not
guarantee the unlocking of encrypted data because nothing can guarantee that
hackers keep their word. Therefore removing this is the best solution.
How to remove it?
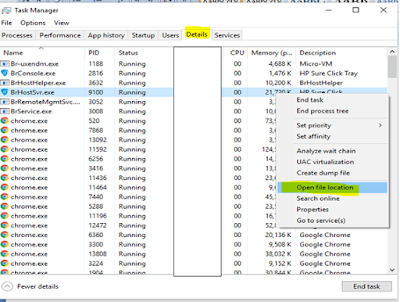
- Press Ctrl
+ Shift + Esc to enter the Task Manager. Go to the Tab labeled Processes
(Details for Win 8/10). Carefully look through the list of processes that
are currently active on your PC. If any of them seems shady, consumes too much
RAM/CPU or has some strange description or no description at all, right-click
on it, select Open File Location and delete everything there. Even if
you do not delete the files, be sure to stop the process by right-clicking on
it and selecting End Process.
2.Open
the Start Menu and type msconfig. If you see any sketchy/shady
looking entries in the list with an unknown manufacturer or a manufacturer name
that looks suspicious as there could be a link between them and .Todarius,
disable those programs and select OK.
3. Get
the Regedit and search for (Ctrl+f) anything name under TODARIUS. If found anything delete them.
4.Type each of the following locations in the Windows search box and hit enter to open the locations:
4.Type each of the following locations in the Windows search box and hit enter to open the locations:
- · %AppData%
- · %LocalAppData%
- · %ProgramData%
- · %WinDir%
- · %Temp%
Delete
everything you see in Temp linked
to .Todarius Ransomware. About the other folders, sort their contents
by date and delete only the most recent entries.
However these solutions may not work in some situations.
Since this is a very recent ransomware a clear solution is not yet deployed. 😕
But you can always refer internet to get
more details about this. And hopefully, a solution will rise to solve this
nasty ransomware completely.
Oh! Almost forgot to tell you. If you search about this on internet you'll find various solutions that saying 'install this and that if you want to remove this ransomware completely'. But my friend most of those solutions are not working (sad reacts only 😒). So please don't get caught to these false products and moreover use internet carefully these days and always check whether your anti - virus is up-to-date. Happy browsing peeps. 👏👏
Cheers!
Keep up the good work 💋